IN THE NEWS – ELIJAH Digest | September 19, 2019
Computer Forensic, Cybersecurity and Managed IT Solutions.
Phishing is a type of cybercrime in which hackers contact you while posing as a legitimate institution or organization in an attempt to get you to provide sensitive or private information. Phishing can occur over the telephone, via a SMS text message, or through email.
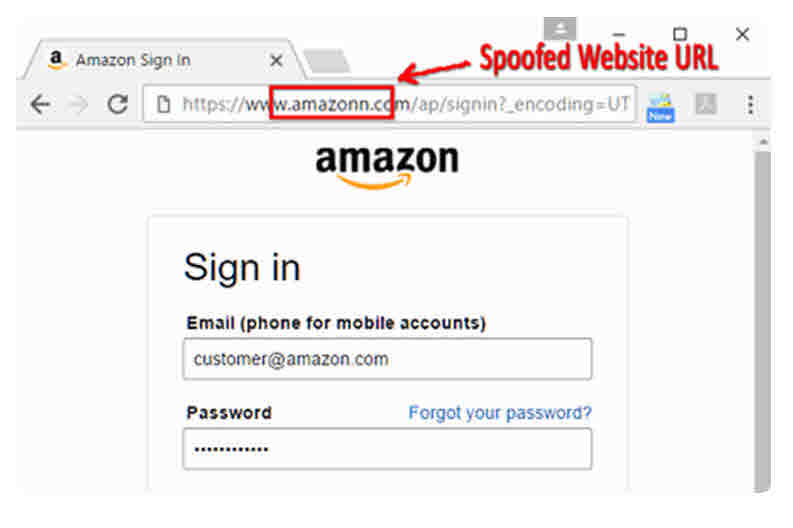
Spoofing is the practice of creating a website or email template that nearly perfectly mimics a legitimate website. Oftentimes, the website design will be very similar but the URL will be slightly off. See an example below:
The Most Common Phishing Scams of 2019 Include:
- Government emails. Emails designed to look like they are from the FBI, IRS, or Medicare or other government agencies are designed to trick you to give away your personal information. Common scams tell you that you are under investigation for “downloading illegal files” or you need to update the government with your correct information. If you are not sure, call the government agency to verify that you were sent an email.
- Fake Tax Emails. Emails such as: “You are being Audited” or “You have been pre-approved for an early refund” are similar types of Phishing scams as in number one above. Remember, the IRS will never call you or send you an email. You would receive a letter in the US Mail.
- Help Me! These messages come from someone claiming to be in a desperate situation that needs your help. Sometimes it comes from strangers, but it may come from a family member or your boss. When in doubt about these messages, call the sender on the telephone.
- Update Your Account! A message from the Bank or a trusted organization may ask you to update your information due to a problem with your account. They provide a link with a legitimate looking sign in portal. Once you sign in, the criminal has your login credentials and full access to your account. Most organizations will not send an email and when they call, there are several layers of security to go thru before you can actually make changes.
- You are a Winner! “Congratulation, you have won a special prize.” We all have dreams of winning the Lottery, but remember, you have to enter the Lottery to win it. You may receive an email telling you that you have won a free vacation, iPhones, or large amounts of cash. Just send your personal information to the sender OR send a deposit to the email address to receive your cash bonus. Never send any information. If you have actually won, you will not have to provide any information or any cash to get your prize.
- Extortion. Often referred to as “sextortion” this scam usually comes in the form of an email sender saying that they have figured something out about you that could be compromising. They may mention things about you that can scare you into thinking that this is real.
- Cloud Files.Spoofed email from Microsoft Outlook or Office 365 will tell you that your account has been hacked and you need to log back into your account to verify that you are who you say you are. Or, you get a message that someone has shared a document with you. Verify the sender’s address carefully to be sure that this looks OK. Better yet, call the sender to verify.
- Package Delivery. You are told that there is a problem with your UPS, FedEx, DHL, or the USPS delivery and that you need to complete more information to complete the delivery. If you provide your personal information, you may be infected with an automatic malware download, causing a major infection on your computer.
- Check this Out! Hackers will send an email that looks like it’s from someone you know. The name will be exactly the same, but the email address will be different, even slightly (i.e. letters in different order or duplicate letters in the email address). To be safe, create a new email and send it to the person that sent you the email, asking them if they sent it to you.
Tips to stay safe from Phishing Scams:
- When in doubt, don’t click.
- Always assume that if something is too good to be true, it usually is.
- Double check the sender’s address and URL’s.
- Contact friends to see if they actually sent you the message.
- Look for spelling errors.
- Work with a team of Cybersecurity & Information Technology professionals for assistance on how to train your employees on how to look out for suspicious emails.
About ELIJAH
Founded in 2003, ELIJAH is a multi-award-winning leader in providing expert digital forensic, data security solutions, and managed IT. ELIJAH is owned and managed by former litigation partners and is an efficient boutique digital forensic, cybersecurity and IT solutions provider that makes clients’ lives easier through effective communication and white glove service. For additional information, please visit https://www.elijaht.com or call 866-354-5240.





























